Pixl Liveness Detection API
Secure Your Users, Enhance Convenience

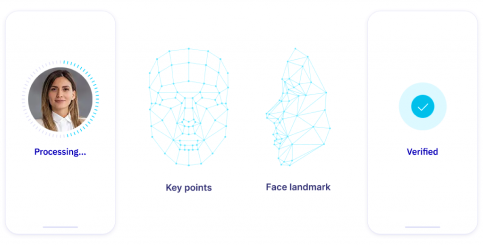
What is Liveness Detection
Liveness detection represents the advanced technology that guarantees the presence of a real person behind the screen. Through this innovative technology, fraud is effectively restricted by accurately monitoring between a live user and fraudulent attempts, such as using a static photo or using malicious applications.
What is Liveness Detection
Effortless Integration:
Integrate Pixl’s API smoothly into your existing applications for a frictionless user experience.
Real-Time Verification:
Guarantee users are physically present during verification, thwarting attempts to spoof identities with photos or videos.
Advanced Anti-Spoofing:
Our robust measures effectively distinguish between real human eyes and sophisticated spoofing tactics.
Multimodal Verification:
Fortify security by combining eye blink detection with facial recognition or head movement analysis.
Customization Options:
Tailor the verification process to your specific needs, including location-based adjustments.


What is Liveness Detection
Liveness detection represents the advanced technology that guarantees the presence of a real person behind the screen. Through this innovative technology, fraud is effectively restricted by accurately monitoring between a live user and fraudulent attempts, such as using a static photo or using malicious applications.

Defend Against Fraudulent Activity
Pixl’s Liveness Detection API shields your platform from fake accounts, safeguarding your users and data.
Instill User Trust
Cultivate a secure environment that fosters unwavering trust and drives heightened user engagement.
Streamline User Onboarding
Expedite the onboarding process with seamless and secure liveness checks powered by our Liveness Detection API.
To perform Pixl Advanced Liveness Detection

Face Matching :
The system compares the user’s face with stored facial records for precise identification.

Liveness Detection :
Verifies the user’s live presence by analyzing natural blinking, live lip movements, and background authenticity.
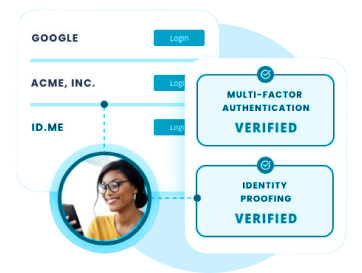
Verification Methods :
Users complete the identity verification process through voice command authentication or on-screen steps.

Decision-Making :
The system meticulously evaluates the verification results, comparing them with previous steps to determine authenticity.
Frequently Asked Questions
